An Overview of Security and Privacy Challenges in Connected Autonomous Vehicles
Keywords:
Connected Autonomous Vehicles, CAVs, Security, Privacy, Cybersecurity, Data PrivacyAbstract
The emergence of connected autonomous vehicles (CAVs) is transforming the way we travel and transport goods. However, as with any new technology, there are significant security and privacy challenges that must be addressed to ensure their safe and widespread adoption. This research study provides an overview of the key security and privacy challenges facing CAVs.
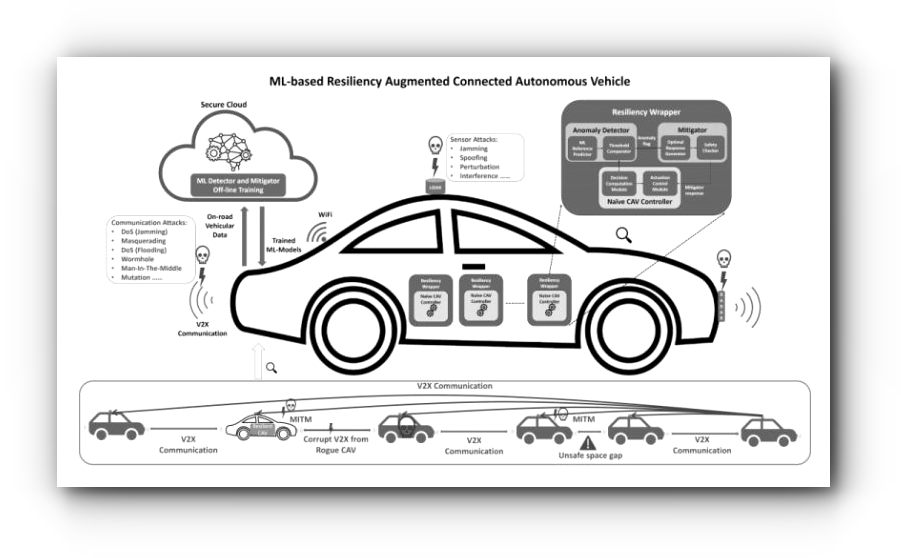
One of the most pressing challenges is cybersecurity. CAVs rely heavily on communication networks to exchange data with other vehicles, infrastructure, and the cloud. This makes them vulnerable to cyberattacks, which could compromise the safety of passengers and other road users. Cybersecurity risks include theft of sensitive data, unauthorized access to vehicle controls, and hacking of sensors and communication systems.Data privacy is another significant challenge. CAVs generate and collect a large amount of data about their surroundings and occupants. This data could be used to track people's movements and habits, and to infer sensitive information such as health status or financial situation. Ensuring that this data is collected and stored securely and used only for its intended purposes is crucial for protecting the privacy of CAV users. As CAVs become more widespread, questions about liability in the event of an accident will become more pressing. Resolving these questions will be crucial for establishing a legal framework that can support the safe and responsible use of CAVs. Human-machine interaction is another challenge facing CAVs. CAVs rely on complex algorithms and machine learning models to make decisions about how to navigate the road.These algorithms can be opaque and difficult for humans to understand, which can create a sense of mistrust and unease. Ensuring that users have a clear understanding of how CAVs work and how to interact with them safely will be crucial for ensuring their adoption. CAVs are physical objects that can be targeted by physical attacks, such as vandalism or theft. Ensuring that CAVs are designed and built with physical security in mind will be crucial for ensuring their long-term viability.CAVs are complex systems that require a range of components, including sensors, processors, and communication modules. Ensuring the security of these components throughout the supply chain is crucial for protecting the overall security of the vehicle.
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2022 Tensorgate Journal of Sustainable Technology and Infrastructure for Developing Countries

This work is licensed under a Creative Commons Attribution-NonCommercial 4.0 International License.