ANALYZING THE EFFECTIVENESS OF BEHAVIORAL BIOMETRICS IN AUTHENTICATION: A COMPREHENSIVE REVIEW
Keywords:
Authentication, Behavioral biometrics, Gait recognition, Keystroke dynamics, Lip motion, Speaker recognition, Voice recognitionAbstract
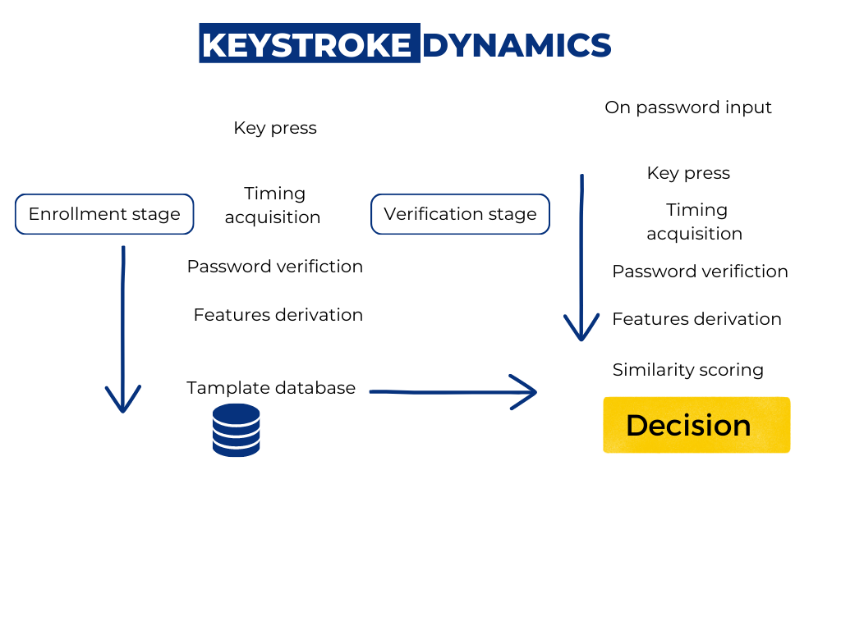
Behavioral biometrics is a rapidly growing area of research that focuses on identifying and authenticating individuals based on their unique behavioral patterns. In this study, we examined the strengths and weaknesses of six commonly used behavioral authentication methods: keystroke dynamics, signature recognition, speaker recognition, voice recognition, gait recognition, and lip motion. Our findings show that each of these methods has unique strengths and weaknesses that make them suitable for different security scenarios and user characteristics. Keystroke dynamics and signature recognition are both based on unique patterns of behavior that are difficult to mimic, making them effective for continuous authentication during login and signature processes. Speaker and voice recognition are based on unique voice characteristics and can be used for continuous authentication during voice-based interactions. Gait recognition is based on unique walking characteristics and can be used for continuous authentication during movement-based interactions. Finally, lip motion is based on unique lip movements and can be used for continuous authentication during speech or lip-based actions. However, our study also identified several weaknesses of these behavioral authentication methods. External factors such as changes in an individual's behavior due to injury, age, or environmental factors such as background noise, lighting conditions, or quality of equipment used, can affect the accuracy of these methods. Additionally, some of these methods may not be suitable for individuals with certain disabilities or who have difficulty with certain behaviors. The study highlights the importance of considering the strengths and weaknesses of different behavioral biometrics methods when implementing security measures. By understanding the unique characteristics and limitations of each method, organizations can make informed decisions about which methods to use and how to combine them effectively to provide strong and reliable authentication.
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2019 Tensorgate Journal of Sustainable Technology and Infrastructure for Developing Countries

This work is licensed under a Creative Commons Attribution-NonCommercial 4.0 International License.